Phishing: A cyber issue on online form
The word “Phish” is pronounced similar to “Fish” which is almost like throwing a baited hook and hoping the victim bites it. Phishing is a method of gathering personal information by using fake e-mails and websites. The attacker who uses this method tries to distribute malevolent links and attachments via his phishing e-mails. The attacker can perform various harmful operations using this method such as gathering personal information and account information of the victims.
What are the types of phishing?
As we mentioned before, various types of phishing exist and they are used to sell somebody the Brooklyn bridge. However, we can sum up the most common purposes of phishing under some categories. One way to categorize phishing activities is by the “purpose” of the phishing activity. Usually, a phishing campaign intent to make the victim do one of two things. These are either making someone hand over his / her sensitive information or making someone download malware in his / her device.
Making the victim hand over his / her sensitive information by trying to trick the user into revealing information data such as usernames, passwords by using which the attacker can reach a system or the victim’s accounts. This method is often used in form applications that are originally produced for the use of businesses and individuals. We will take a closer look at the relation between phishing activities and form applications in the following paragraphs of this article.
Making the victim download malware in his / her device and by doing this, infecting the victim’s computer. This malware attack is generally delivered via phishing e-mails.
While the purposes of phishing are stated above, various types of phishing are like below:
- Spear phishing; refers to the activity of phishing when the attackers try to create a message for a particular individual to bait the victim. Phishers who use this method identify their victims by checking them out on websites such as LinkedIn. They generally send e-mails which are similar to the victim’s co-workers’ and demand a large bank transfer.
- Whaling / CEO Phishing; refers to a type of phishing that is aimed at a very big fish such as CEOs and other high-value targets. The intention of this type of phishing is stealing data, employee information, and cash.
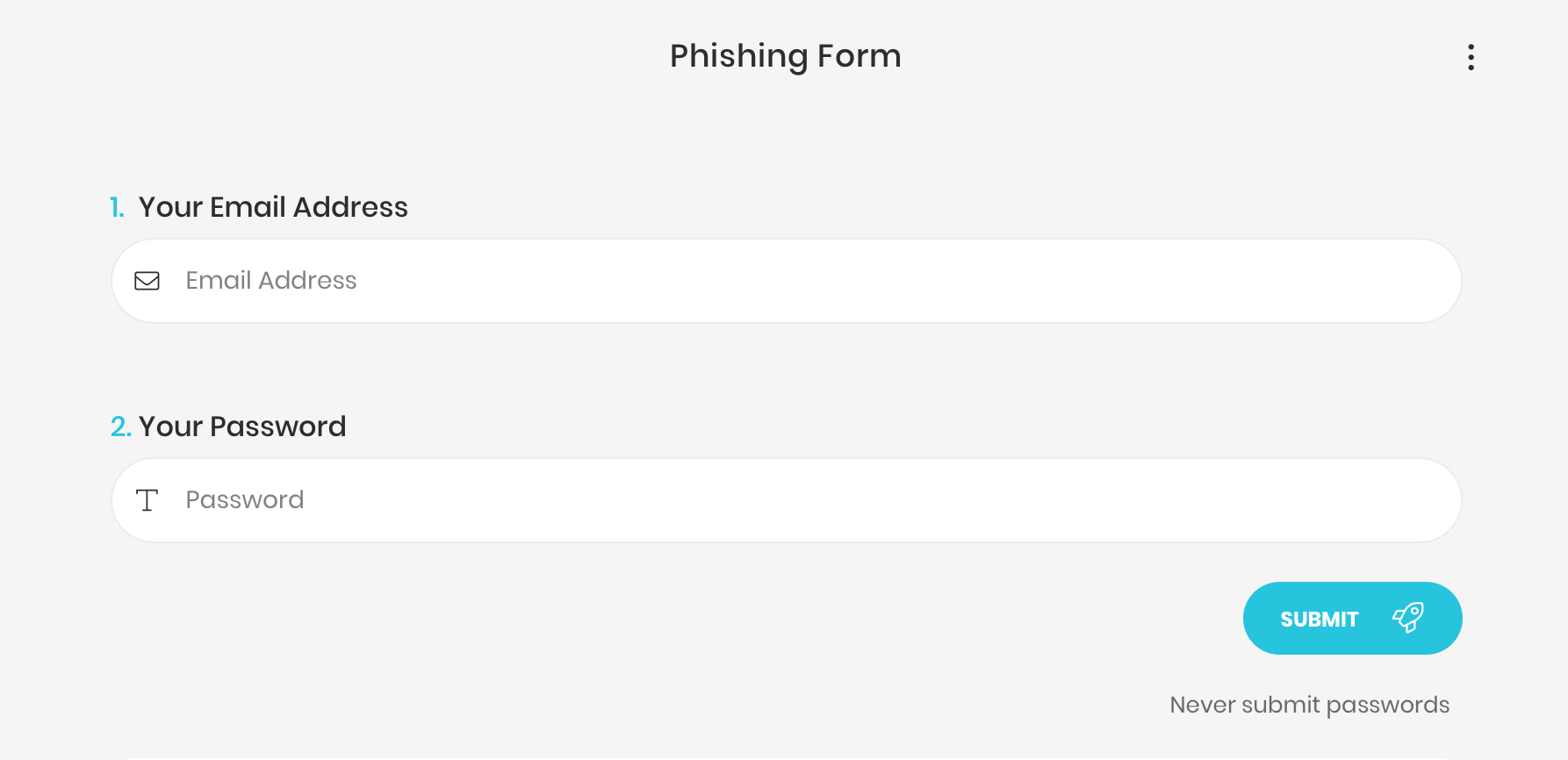
What is a phishing form?
One of the most common ways of phishing is a method of phishing, which is done using form applications. Attackers most commonly create a form related to a specific topic or organization. In these forms, they demand personal information, passwords or online banking credentials. They distribute these forms via their phishing e-mails or even some people are deceived by publicly shared phishing forms without getting into any interaction with the attacker.
How to avoid phishing forms
Avoiding phishing forms is a demanding part of using form applications. Attackers mostly use form applications for deceiving people into revealing confidential information and obtaining access to various assets of the victims. They generally do this by masquerading as someone from the company where the victim works or the bank where the victim has an account. In order to avoid this type of cases, users must be more careful. They should check whether their co-workers or bank staff contact them via some suspicious e-mails and ask for confidential information such as passwords, online banking credentials and personal information. For this reason, form application users should choose an application that provides both the businesses and individuals with a high level of security. As a matter of fact, people who fill any form on any form application must be aware that they should not be revealing any confidential information.
What does “safe form” mean?
The term safe form refers to a form that is created and went through a process of security procedures. These procedures commonly consist of processes such as checking the published forms manually to figure out whether any of them is subject to phishing activity. At this moment, phishing is a major security issue and a financial burden for almost every one of the form applications, as the manual techniques require a lot of time, work, and extra employees.
You are safe on forms.app
Similar to the other form applications’ situation, plenty of phishing attackers use forms.app in order to create phishing forms and by doing this, they try to scam many innocent people. However, forms.app is one of the best on the market in terms of security precautions and protecting users from revealing their confidential information via the forms created on forms.app application. forms.app doesn’t keep phishing forms. These phishing forms are deleted by the specialists of this particular issue as soon as they are published. Also, the users who publish these scamming forms are banned from using forms.app permanently. In light of this information, it can be easily said that forms.app users are safe on forms.app and they will be so, as we are working hard for improving security levels and preserving our users from any harm that might possibly come from phishers!